Tu N. Nguyen
Advanced Machine Learning Approaches for Enhancing Person Re-Identification Performance
Jan 04, 2026Abstract:Person re-identification (ReID) plays a critical role in intelligent surveillance systems by linking identities across multiple cameras in complex environments. However, ReID faces significant challenges such as appearance variations, domain shifts, and limited labeled data. This dissertation proposes three advanced approaches to enhance ReID performance under supervised, unsupervised domain adaptation (UDA), and fully unsupervised settings. First, SCM-ReID integrates supervised contrastive learning with hybrid loss optimization (classification, center, triplet, and centroid-triplet losses), improving discriminative feature representation and achieving state-of-the-art accuracy on Market-1501 and CUHK03 datasets. Second, for UDA, IQAGA and DAPRH combine GAN-based image augmentation, domain-invariant mapping, and pseudo-label refinement to mitigate domain discrepancies and enhance cross-domain generalization. Experiments demonstrate substantial gains over baseline methods, with mAP and Rank-1 improvements up to 12% in challenging transfer scenarios. Finally, ViTC-UReID leverages Vision Transformer-based feature encoding and camera-aware proxy learning to boost unsupervised ReID. By integrating global and local attention with camera identity constraints, this method significantly outperforms existing unsupervised approaches on large-scale benchmarks. Comprehensive evaluations across CUHK03, Market-1501, DukeMTMC-reID, and MSMT17 confirm the effectiveness of the proposed methods. The contributions advance ReID research by addressing key limitations in feature learning, domain adaptation, and label noise handling, paving the way for robust deployment in real-world surveillance systems.
Characterizing and Understanding Energy Footprint and Efficiency of Small Language Model on Edges
Nov 07, 2025



Abstract:Cloud-based large language models (LLMs) and their variants have significantly influenced real-world applications. Deploying smaller models (i.e., small language models (SLMs)) on edge devices offers additional advantages, such as reduced latency and independence from network connectivity. However, edge devices' limited computing resources and constrained energy budgets challenge efficient deployment. This study evaluates the power efficiency of five representative SLMs - Llama 3.2, Phi-3 Mini, TinyLlama, and Gemma 2 on Raspberry Pi 5, Jetson Nano, and Jetson Orin Nano (CPU and GPU configurations). Results show that Jetson Orin Nano with GPU acceleration achieves the highest energy-to-performance ratio, significantly outperforming CPU-based setups. Llama 3.2 provides the best balance of accuracy and power efficiency, while TinyLlama is well-suited for low-power environments at the cost of reduced accuracy. In contrast, Phi-3 Mini consumes the most energy despite its high accuracy. In addition, GPU acceleration, memory bandwidth, and model architecture are key in optimizing inference energy efficiency. Our empirical analysis offers practical insights for AI, smart systems, and mobile ad-hoc platforms to leverage tradeoffs from accuracy, inference latency, and power efficiency in energy-constrained environments.
NOMA-enabled Backscatter Communications for Green Transportation in Automotive-Industry 5.0
Mar 10, 2022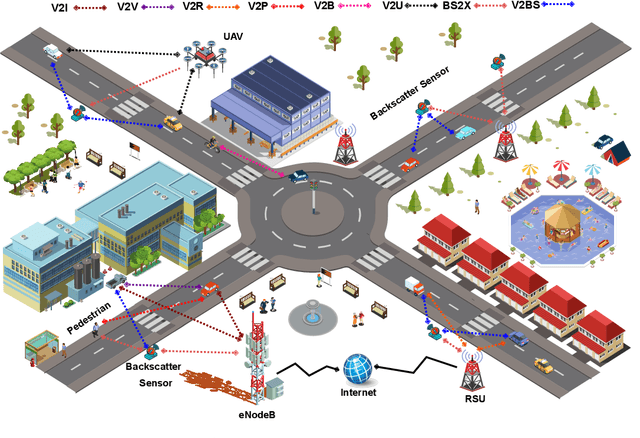
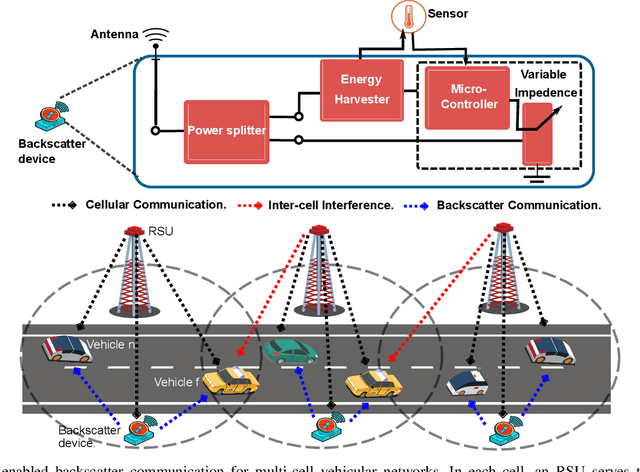
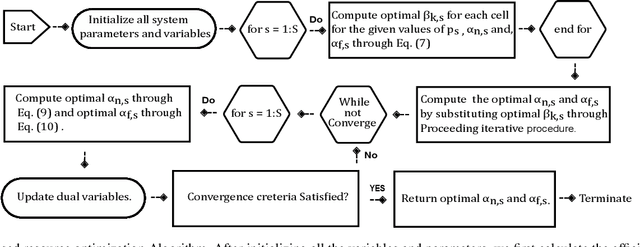
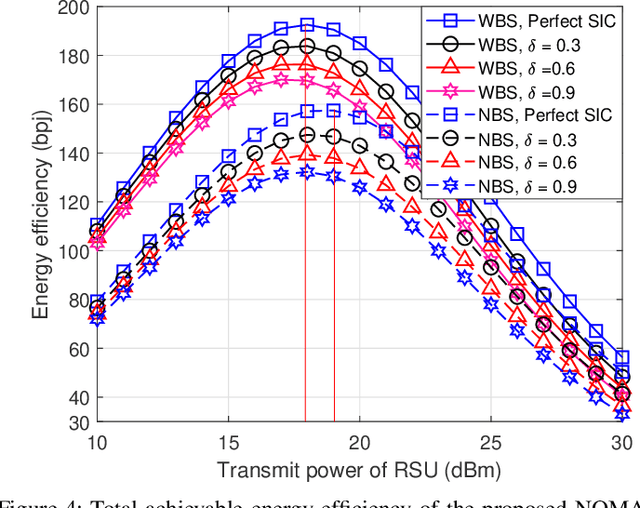
Abstract:Automotive-Industry 5.0 will use emerging 6G communications to provide robust, computationally intelligent, and energy-efficient data sharing among various onboard sensors, vehicles, and other Intelligent Transportation System (ITS) entities. Non-Orthogonal Multiple Access (NOMA) and backscatter communications are two key techniques of 6G communications for enhanced spectrum and energy efficiency. In this paper, we provide an introduction to green transportation and also discuss the advantages of using backscatter communications and NOMA in Automotive Industry 5.0. We also briefly review the recent work in the area of NOMA empowered backscatter communications. We discuss different use cases of backscatter communications in NOMA-enabled 6G vehicular networks. We also propose a multi-cell optimization framework to maximize the energy efficiency of the backscatter-enabled NOMA vehicular network. In particular, we jointly optimize the transmit power of the roadside unit and the reflection coefficient of the backscatter device in each cell, where several practical constraints are also taken into account. The problem of energy efficiency is formulated as nonconvex which is hard to solve directly. Thus, first, we adopt the Dinkelbach method to transform the objective function into a subtractive one, then we decouple the problem into two subproblems. Second, we employ dual theory and KKT conditions to obtain efficient solutions. Finally, we highlight some open issues and future research opportunities related to NOMA-enabled backscatter communications in 6G vehicular networks.
A Convolutional Transformation Network for Malware Classification
Sep 16, 2019
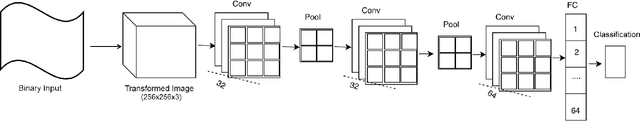
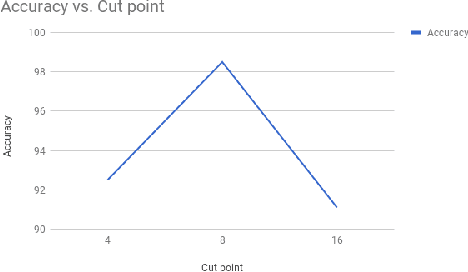
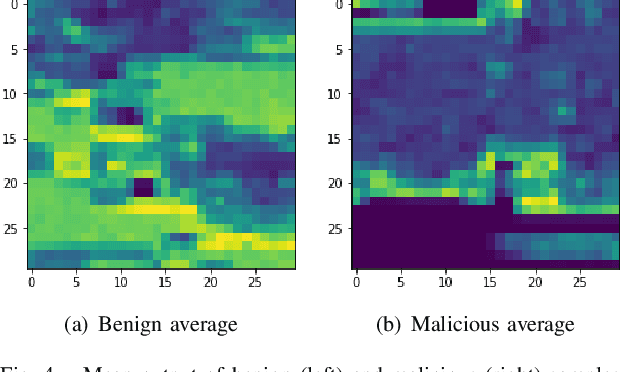
Abstract:Modern malware evolves various detection avoidance techniques to bypass the state-of-the-art detection methods. An emerging trend to deal with this issue is the combination of image transformation and machine learning techniques to classify and detect malware. However, existing works in this field only perform simple image transformation methods that limit the accuracy of the detection. In this paper, we introduce a novel approach to classify malware by using a deep network on images transformed from binary samples. In particular, we first develop a novel hybrid image transformation method to convert binaries into color images that convey the binary semantics. The images are trained by a deep convolutional neural network that later classifies the test inputs into benign or malicious categories. Through the extensive experiments, our proposed method surpasses all baselines and achieves 99.14% in terms of accuracy on the testing set.
 Add to Chrome
Add to Chrome Add to Firefox
Add to Firefox Add to Edge
Add to Edge